What we do?
Your network and data need protection. We’ve got you covered.
Do These Cybersecurity Challenges Sound Familiar?
It’s Complex
It’s tough to understand exactly what’s happening across your network, even when you invest a lot of time and effort. We can give you a clear view of your entire security posture in a user-friendly portal. It’s a straightforward view of everything you need.
It’s Costly
Setting up your own Security Operations Centre (SOC) and keeping it and your team up to date is expensive. If you operate in several locations, your costs skyrocket. We’ve already scaled to locations around the world, and invested in our SOC so you don’t have to.
There’s a new, WFH reality
Traditionally, IT security companies protected you on one, maybe two networks. No more. With staff working from home, most companies use multiple networks. We’ll protect any corporate-owned device, wherever it is.
Threats are unpredictable
Security threats shift quickly, but It takes time to learn from them and prepare for the next one. That’s why deep experience in this sector matters. It’s the difference between recognizing a threat and letting it slip by. We have the experience you need.
We Designed a Solution Just For You
The best sports teams have defensive and offensive lines. That’s what you need if you want to operate safely in today’s online world. Our system protects you from breaches, detects rare threats that penetrate your system, and contains them quickly.
Defensive Security
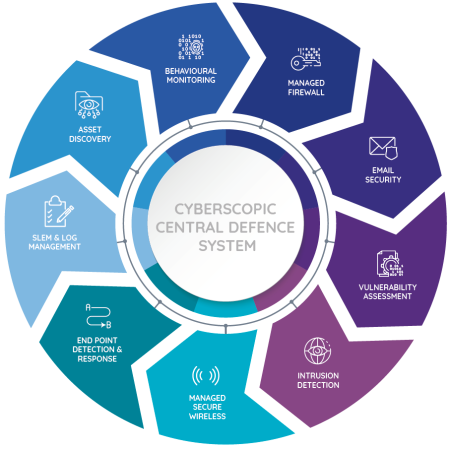
This is our prevention, detection, and response branch. As a managed security operations centre (SOC), we provide these critical security services:
This is antivirus software on steroids. We use machine learning to detect and intelligently prioritize malicious activity so our analysts spend time investigating the right threats.
We compare logs from hosts, servers, and network systems against the latest threat intelligence. Threats are analyzed and prioritized before we move to next steps.
Our service includes the comprehensive discovery of every asset on your network. It’s essential that we understand the attack vectors that already exist in your network.
Our system understands what constitutes normal behaviour in a host. When it knows how a host or device is supposed to behave, it can identify strange behaviour.
We’ll analyze your Office 365 logs to identify administrative changes, rule changes, and other uncommon behaviours that warrant attention.
We’ll look for intrusions into servers and workstations and hacker footholds that already exist, and contain these threats before building further defenses.
This is cloud-delivered security when and how you need it. It’s multiple security functions in one solution, so you can protect devices, remote users, and distributed locations.
Offensive Security
Some people call this ‘ethical hacking’. Our team tries to break into your system to test its defenses and pinpoint weak spots before real hackers find them. We keep a firewall between our offensive and defensive teams. If one hand knows what the other is doing, ethical hacking isn’t as effective. The point is to simulate real-world threats.
Why do we try to hack your system instead of simply waiting for security alerts?
We conduct penetration testing in five areas to see how far into your system we can get:
01
Vulnerability Assessments
02
Web Application Penetration Testing
03
Internal Network Penetration Testing
04
External Network Penetration Testing
05
Open-Source Intelligence (OSINT) Investigation
Your organization will receive one free ‘test and reset’ in each area during your first year with Cyberscopic.
Our Services Include

Monitoring Service
24/7 round the clock monitoring services.

In-House Operations
We don’t rely on third parties.
Around-the-sun coverage
Offices in Canada, Portugal, Brazil, and Malaysia.
Multi Language
Service in English or Portuguese.
Tests and Retests
Five free ‘tests and retests’ from our offense team in your first year.